customer support: sales@itsalliances.com
customer support: sales@itsalliances.com
Vulnerabilities in healthcare systems can expose protected health information (PHI) and lead to costly breaches, but staying ahead of risks is critical. ITS Alliances HIPAA Vulnerability Management service delivers a proactive, healthcare-focused approach to identifying, prioritizing, and mitigating vulnerabilities, ensuring HIPAA compliance and safeguarding patient trust. Our AI-driven security management tools empower your organization to maintain a secure environment with confidence and efficiency.
Leverage AI-powered scans to detect vulnerabilities across your network and applications in real-time, ensuring no weakness compromises PHI security.
Receive tailored, severity-based action plans to address critical vulnerabilities first, optimizing resources and minimizing exposure to cyber threats.
Align remediation efforts with HIPAA Security Rule, reducing regulatory risks and ensuring audit-ready documentation for healthcare compliance.
Stay ahead of evolving cyber threats with ongoing monitoring and updates, protecting your organization from breaches and enhancing operational resilience.
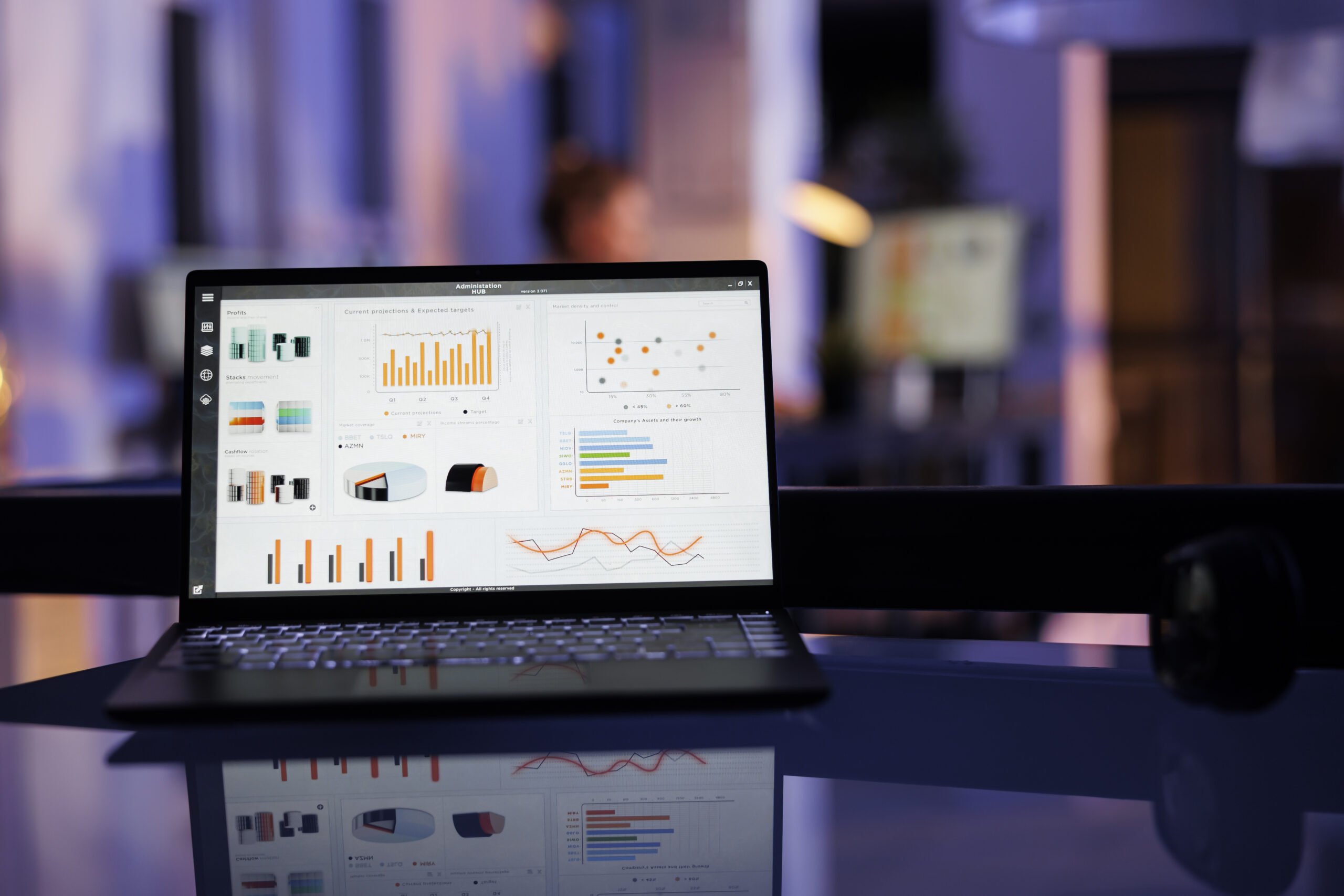
Our platform provides a Cloud-enabled vulnerability scanner agent that is easy to install and customize to fit an organization’s asset monitoring needs that empowers IT security personnel to track, manage, and build a robust security posture.

Analyze scan results to rank vulnerabilities by severity and impact. Our experts provide clear priorities to focus on critical threats first.
With each scan it quickly isolates missing software patches, operating systems patches, configuration errors, and deviations from security policies. The software includes a distributed task and workflow management system and prioritized risk remediation plans.

Customize your scan scheduling and monitor any place, anytime. Our software offers comprehensive data reports and audit logs. Easily create run schedules and distribution lists. Save output for audits and evidence of compliance for POAM (Plan of Actions and Milestones).